


Covid-19, and resulting legislations, ordinances, and Health Advisories have all-but-forced businesses, employees, and contractors in America, and the round the world, to embrace remote work (i.e. working from home) as never before.
In the scramble to keep operations running and businesses afloat, amidst frequently-changing government advice and a veritable patchwork of applicable laws and ordinances, many companies/organizations have adopted new hardware, software, and procedures without their usual attention-to-detail regarding their own security practices and those of their (often new) vendors.
While most business owners and system administrators are keen to check website address bars for a lock (indicating that HTTPS/SSL security is in place for connections a vendor’s website(s), once users download and run a vendor’s software to their computers, or a vendor’s app to their phones, the security of communications to/from the vendor may not be as apparent to the untrained eye, and even to many trained technology professionals.

One solution many businesses have turned to, in an effort to secure and to standardize the communications of staff who are working from home, is the implementation of a VPN (Virtual Private Network).
VPNs, as used by most remote workers, may come in one of two forms:
In most VPN current remote-worker use-cases, the connection of choice for most companies is a Client VPN. The reason for this is that such are (usually) location-independent and (if company policies and the software used allow) may even be device-independent.
As a result, Client VPN users are often able to, with a single account (username/password), secure their some or all of their data communications across a computer, a mobile phone, a tablet, or any other device running Microsoft Windows, Linux, Apple OSx, Apple iOS, or Android. In the cases of iOS and Android users do not even need to install new apps to connect to many corporate Client VPN services, as the most common connection and encryption methodologies come already “built-in” to this operating systems.
For Desktop and Notebook computer users, they may be required by employer to install one of several applications specific to the VPN platform they employ. Examples of these may include Cisco’s AnyConnect Client, Sonicwall’s SSL or Global VPN clients, the OpenVPN client, or others.
Depending on the way that System Administrators for a given organization configure their VPN platform and end-user clients, the user may have one of two very different experiences.
Split Tunneling represents a data flow model which only applies VPN encryption to data to/from resources controlled by the employer, leaving normal web browsing, third-party apps, and private email traffic outside the curtain of VPN protection and encryption.

Full Tunneling indicates a VPN data flow model which routes all internet communications through the Virtual Private Network controlled or contracted by the employer/contracting organization.
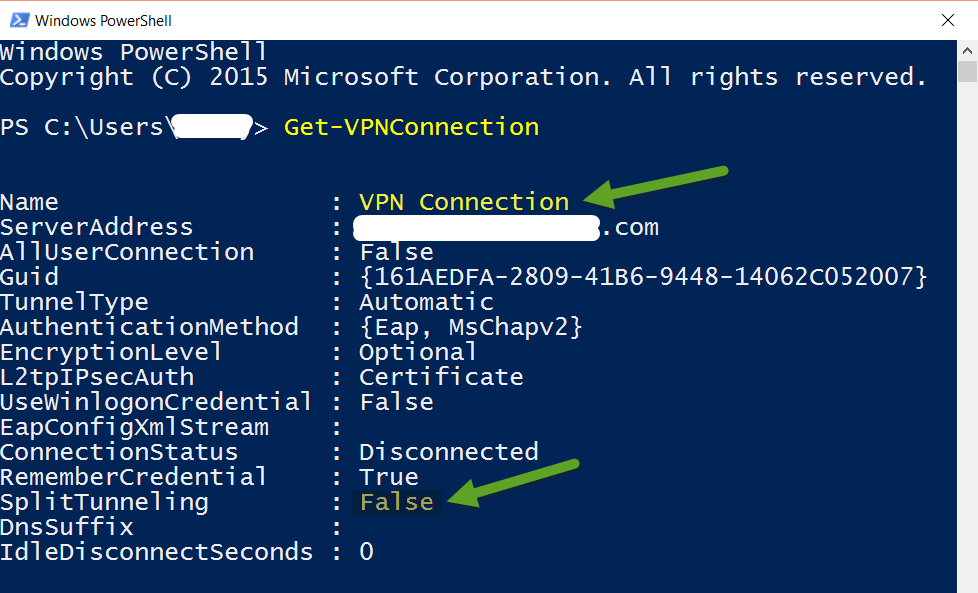
Clearly, two very different tiers of security, and of end-user-privacy, are indicated by the above, with pros and cons in either direction.
In the case of Split Tunneling, an employee may rest assured that their private communications are (all else being equal) secure from VPN-based “snooping” by an employer. This may include Facebook use, Instagram use, Twitter use, Skype use, Gmail use, web browsing patterns, and more.
Full Tunneling, in stark contrast to the above, routes (again; all else being equal) all internet communications through the connected VPN service, encrypting connections and communications before they leave the device in question, offering the end user certain protections across all services and internet-connected applications used from the VPN-connected computer, phone, or tablet.
Of course, with the protections described, come concerns for the average end-user which may include, but certainly are not limited to, the potential ability of an employer to monitor private communications. chats, and web browsing habits across all devices leveraging the organization’s VPN service.
Separate from Client VPN is another Virtual Private Network type called “Site to Site VPN”. This type of VPN connection utilizes (in most cases) a dedicated piece of hardware at the “Remote” location which maintains a persistent connection to a corporate or centralized network irrespective of whether or not the end-user is making use of the connection at a given moment (although many may conserve resources by disconnecting after a given period of disuse, by design). Such a VPN connection generally allows for one or more remote end-user devices to connect to a dedicated (company-supplied) network appliance within their “home”, which then may inspect, encrypt, and protect all communications which pass through it to the corporate environment.
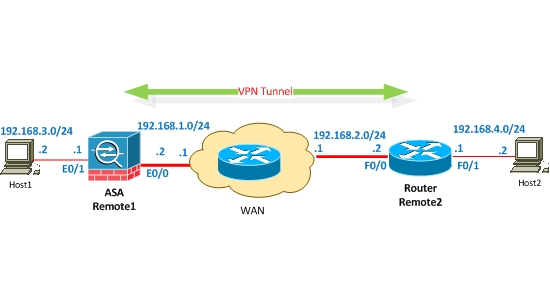
Such connections, as one may imagine, do not (generally) leave the end-user with a method to “hide” personal data communications and internet activity from an employer, as the employer generally maintains sole control over communication logging and filtering via the device supplied.
A modern competitor to VPN is SDP (Software Defined Perimeter). Most SDP schemes involve a so-called “Zero Trust” methodology to approving connections and communications to corporate resources.

What this means, in practice, is that while a VPN user, once connected, may often (but not always) gain access to all network resources within the connected TCP/IP scope, unless expressly denied access, SDP does the opposite, forbidding communications with all internal network resources except those expressly allowed, per the policy applied to the user or device.
Because traditional VPN connections tend to be permissive, with regard to network resource access once connected, a malicious user or malware may employ one or more network scanning and attack methods against a wide range of corporate targets. A Software Defined Perimeter is intended to eliminate this vulnerability by blocking all access except to/from per approved resources, severely reducing the possible scope of an attack via one or more connected systems.
SDP, as one may suspect, carries more administrative overhead, but offers nominally enhanced security with regard to multi-target attacks from a single connected user or end-user device.
VPN and SDP, while offering a host of benefits each, do both share a common security concern which may keep some System Administrators and Business Owners up at night, however. These include Viruses, Malware, Ransomware, and other threats from an infected end-user’s computer, tablet, or smartphone, as well as malicious end-user activity.
Once a device is connected and approved for communication to one or more internal resources via VPN (whether Client VPN or Site to Site VPN), the same danger applies. If an end-user’s device is infected by a Virus, Malware, or Ransomware, the same malicious program may often impersonate the end user, gaining access to all files, folders, databases, and other network resources the end-user is typically granted access to.
Using the access described above, Ransomware may then proceed to encrypt corporate files, Malware and Viruses may spread to other computers within the network, or a Virus may simply perform a Denial of Service (DoS) attack against corporate servers, rendering them temporarily unusable by staff or even causing them to crash entirely.
In addition corporate information may be “stolen”, which could include Social Security Numbers and home addresses of staff, financial documents including bank account numbers and credit card numbers, or (in the case of healthcare organizations) may involve the illegal obtaining of Personally Identifiable Health Information, which may constitute a HIPAA (The Health Insurance Portability and Accountability Act) violation, potentially resulting in hefty fines from the United States Government’s Health and Human Services division.
One methodology preferred by many security-conscious organizations is Remote Desktop (also referred to as Terminal Services).
While Remote Desktop is often associated with Microsoft’s RDP (Remote Desktop Protocol), Microsoft if far from the only software vendor which offers such a solution, with notable alternatives being offered by Citrix, Parallels, and even Google.
The core user-facing methodology, however, remains the same. The end-user in a Remote Desktop scenario connects to a centralized server (or “Server Farm”) for authentication and connection, after which the centralized server acts as the “Computer” the end-user works within.
Most Remote Desktop platforms permit System Administrators to control which types of end-user-connected devices and resources may communicate with the centralized server, with keyboard strokes, mouse movements, mouse clicks, and video being the general minimum transmitted. In permissive scenarios, however, any number of other peripherals, folders, speech, music, and other elements may be allowed to traverse the connection.
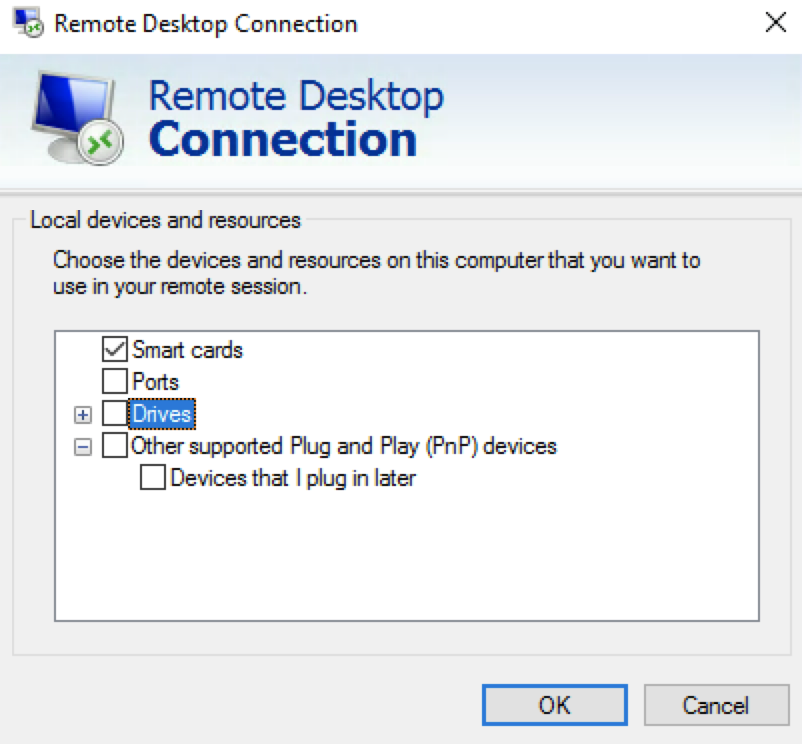
Remote Desktop connections may use any number of TCP (Transmission Control Protocol) ports, depending on software vendor, but modern implementations tend to favor connectivity over port 443 (generally associated with Secure Sockets Layer communication), which most internet service providers and corporate networks leave unblocked by default.
Once a user is connected to (and is utilizing) a properly secured Remote Desktop solution, their primary activities and data communications are all-but-indistinguishable from communications to/from a “corporate office”, as far as internet service are concerned.
In addition, when properly secured, most malware infections affecting an at-home end-user device are not able to compromise corporate resources within a secure corporate perimeter.
All of them – and none of them – but Amerihub prefers Remote Desktop

As with any technology solution, the solution is only as secure as its configuration makes it – and that can be a moving target, especially in 2020.
That is part of why we, at Amerihub, prefer Remote Desktop methodologies over VPN and SDP for users who work from home. There are fewer moving parts to manage and to secure.
A Remote Desktop server allows System Administrators to install and to secure an application once, on one system, after which is it “instantly” available to all connecting users. Similarly, Sysadmins are able to filter and to monitor internet communications to/from one server or server farm, within a secure perimeter, with these protections encompassing all users at one time – while VPN and SDP requires non-insignificant maintenance and security hardening of end-user devices (some of which may not be owned by the organization itself).
What Should I do Next?
Regardless of which Remote Worker solution you prefer (VPN, SDP, or Remote Desktop), Amerihub is prepared, experienced, and is capable of rapid and secure implementation of the same for companies across the globe, with server/centralization resources in multiple global regions.